
Perimeter 81 Software-Defined Perimeter
User-centric network architecture

Perimeter 81 Team Members Essentails per user/month (5 user minimum)
Our Price: Request a Quote
Transcend the traditional VPN. Defend and modernize your network with the latest architecture and seamless least privilege access.
Team Members (Essentials)
Team Member (Essentials) licenses are necessary for each account user with a unique email address. Each team member should have their own user license. Users can access their Perimeter 81 account on up to 5 devices (desktop, mobile and tablet) at no additional charge. You can have as many team members as you do purchased licenses.Team Members (Premium)
Team Member (Premium) licenses offer all the capabilities of Team Member (Essentials) tier plus the following capabilities: Agentless application Access (up to 20 applications for micro-segmented policy setting), increased Activity audits & reports retention (30 days retention versus 14 days for Essentials), access to shared public gateways (useful for clients traveling abroad that want low latency connections), Single Sign On integrations (integrate with client Identity Provider to provide simpler user authentication), and Always-on VPN (administrators can enforce user endpoints to always keep client connection active).Private Gateways
A private gateway licenses providers a private cloud server dedicated solely to your company. By deploying a private gateway through the management platform your team members can share a single static outgoing IP address only accessible by your organization's authenticated users. Gateways allow for secure and granularly segmented team member access to on-premise network resources, cloud environments, and Zero Trust applications. Each gateway can support normal data traffic for up to 100 concurrent team member users. You may consider adding more gateways to support higher volumes of concurrent users or to add additional geographies where users are located.The Software-Defined Perimeter (SDP) is a sophisticated architecture that is reshaping the future of network security. Our software-defined perimeter solution offers simple cloud migration security, seamless least privilege access to resources and secured access to cloud environments - including IaaS, PaaS, and more.
What is a Software-Defined Perimeter?
The traditional perimeter-based approach to network security isn’t enough. To adequately protect their data, businesses are turning to a new approach - the Software-Defined Perimeter.
What Is a Software-Defined Perimeter?
Implementing SDP allows organizations to restrict network access and provide customized, manageable and secure access to networked systems.
Connectivity is based on the need-to-know-model, meaning each device and identity must be verified before being granted access to the network.
What Does a Software-Defined Perimeter Do?
An SDP solution allows IT Managers to deploy gateways on-premise or over the cloud, securing employees’ remote access to cloud and on-premise applications, all while keeping sensitive data within the organizational network. It has been shown to stop all forms of network attacks including DDoS, Man-in-the-Middle, Server Query (OWASP10) and Advanced Persistent Threat.
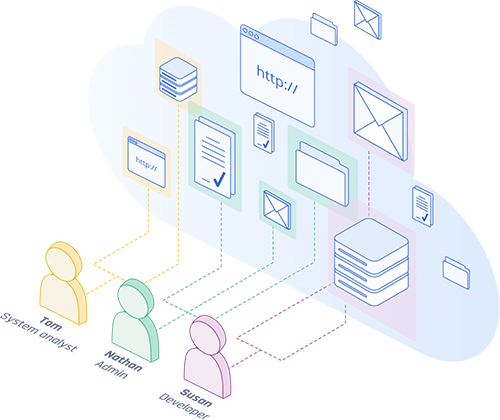
Securing a Digital Workspace
SDPs protect networks and critical assets from external threats.
Adaptive
With an SDP, you can implement automated policies that dictate which device, user and service is able to access the network.
Global Access
Using an SDP, you can deploy unified gateways, giving access to any resources, from any location. This provides connectivity for remote and on-premise users.
Precise Segmentation
SDPs integrate with any Identity Provider, including Active Directory and SAML services, allowing you to utilize precise segmentation.
Secured & Encrypted
To ensure total privacy, data security and classification, SDPs provide client and endpoint protection, identity and access management, OS and application level security, all while encrypting traffic with mutual TLS encryption.
How Does a Software Defined Perimeter Work?
![]()
SDP Client - Access Control
The client verifies each user's identity and routes whitelisted applications to authorised remote applications. This real time configuration ensures the certificate-based mutual TLS VPN only connects to authorised services. Network traffic is encrypted and tunneled between the user's device until reaching the corresponding SDP Gateway.
![]()
SDP Controller - Trust Broker
The controller establishes trust between the SDP Client and backend security controls by authenticating users and devices. By evaluating the controller, Issuing Certificate Authority and Identity Provider, the user and network entitlements are verified, the SDP Controller configures the gateway in real time to provision a mutual TLS connection.
![]()
SDP Gateway - Termination Point
The set of gateways grants access to previously private resources. This termination point for the mutual TLS connection from the Client verifies the identity of the requesting device, authorizes the user, and grants access to the requested network.
Why Enterprises Are Moving to a Software-Defined Perimeter
Transitioning to the cloud presents new vulnerabilities that can significantly impact an organization's security.
Replace labor-intensive and inconvenient VPNs, Firewalls, and NACs
While perimeter-based network security tools are effective at the bare minimum security standards, these tools fail to full protect data and provide customized access for individual users. Users often have too general network access. If breached, this could give cybercriminals the ability to penetrate and move laterally across your private network.
Ensure compliance through secure, policy-based access
Secure network segmentation that creates one-to-one network connections between the user and the resources they access. Everything else is invisible - including the system itself. This not only applies the principle of least privilege to the network, but also reduces the attack surface area by hiding network resources from unauthorised users.
Grant on-premise and remote network access
Tedious hardware installations and hours of help desk support are now a thing of the past. With a Software-Defined Perimeter architecture and comprehensive management platform, gateways can be automatically deployed in any location, enabling simplified network security and IT management.
Discover How SDP Technology Can Transform Your Business
With Perimeter 81, our mission is to provide secure, private and unrestricted Internet access to businesses of all sizes and industries.
Our Software-Defined Perimeter architecture offers:
- Complete visibility
- Precise segmentation
- A highly scalable solution
- A user-centric experience
- Simple transition to cloud environments

