
Zero Trust Security
What is a Zero Trust Security?
Legacy security models are no longer effective against sophisticated cyber threats, globalization, and user mobility.
With Zero Trust security, policy enforcement and protection are easily implemented by isolating applications and segmenting network access based on user permissions, authentication, and verification.

The Benefits of Adopting Zero Trust Principles
Zero Trust security promotes several technical and business advantages.
![]()
Mitigate Data Loss
Dramatically enhance your security posture and mitigate data loss via visibility, safe enablement of applications and threat prevention.
![]()
Increase Efficiency
Simplify compliance with highly effective trust boundaries by segmenting sensitive resources with security and privacy mandates.
![]()
Enable Mobility & Virtualization
Increase the ability to accommodate transformative IT initiatives such as cloud computing, infrastructure virtualization, user mobility and more.
![]()
Increase Visibility & Security
Segment a single network into small perimeters to increase security, monitoring, and visibility while reducing support and spending.
The Zero Trust Model - How it Works
Internal networks are comprised of different levels of “trust boundaries” which should be segmented according to sensitivity.
Network Segmentation
Network segmentation allows organizations to define internal trust boundaries to granularly control traffic flow, enable secure network access and implement network monitoring.
Management Infrastructure
Efficiently monitor the network via centralized management capabilities, allowing data to be processed by tools that may further enhance network visibility, detect unknown threats, or support compliance reporting.
Trust Zones
Trust zones are comprised of distinct pockets of infrastructure where resources operate at the same trust level and similar functionality such as protocols and types of transactions, minimizing pathways and limiting malicious threats.
Application Access
Secure application-level access by fully auditing, recording and monitoring each session. This reduces the attack surface and provides a distributed security solution which operates as a holistic threat protection framework.
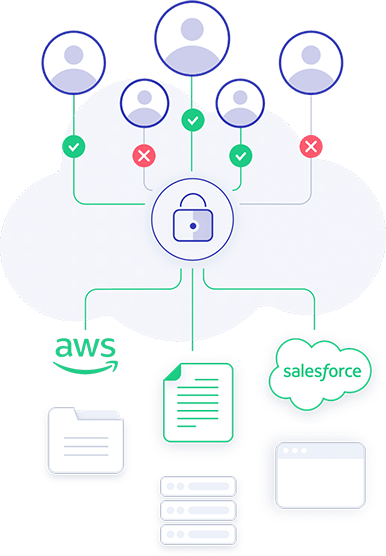
Getting Started with Zero Trust Access
It's not necessary to wait for the next network and security infrastructure - with Perimeter 81 implementation becomes attainable and manageable.
![]()
Secure Network Access
Network security, implemented via a client application for endpoints, allows for secure IPsec and SSL VPN connectivity for all employees, partners, customers and guests no matter where they're connecting from (e.g., remotely, the local network, or the Internet).
![]()
Inspect and Log ALL Traffic
Identify and classify all traffic, regardless of ports and protocols, encryption or hopping. This eliminates methods that malware may use to hide from detection and provides complete context into applications, associated content and threats.
![]()
Least Privilege Access Control
With a least-privileged strategy and strictly enforced access control, organizations can control interactions with resources based on relevant attributes, including application access, user and group identity and the sensitivity of the data being accessed.
![]()
Advanced Threat Protection
Legacy technology can't distinguish between specific applications. With Perimeter Zero, comprehensive protection supports a closed-loop, highly integrated defense stature that consistently and cost-effectively enables trust boundaries.
![]()
High-Performance Design
Perimeter 81's zero trust solution minimizes latency and surpasses processing requirements, providing high availability, avoiding loss of service, reducing redundant loads on servers and increasing the uptime of your network.
![]()
Comprehensive API Integration
A comprehensive REST-based API that enables quick-and-easy integration with third-party management, automation and orchestration tools - for example, to ensure protection for newly provisioned or relocated virtualized applications.
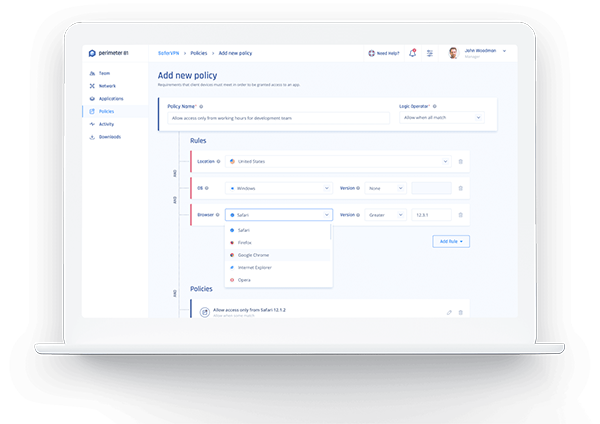
Convert to Zero Trust on the Fly
Migrate to Zero Trust network security with a highly flexible, non-disruptive solution.
Organizations can feel confident that they can implement Zero Trust security without needing to modify their existing networks.
With Perimeter 81, your organization can non-disruptively transition to a Zero Trust model with a completely transparent experience for all users.

