
Perimeter 81 Zero Trust Application Access
Ensure secure, zero-trust access to web applications, SSH, RDP, VNC or Telnet, through resilient IPSec tunnels - without an agent

Perimeter 81 Team Members Essentails per user/month (5 user minimum)
Our Price: Request a Quote
Reduce the attack surface. Implement zero-trust, fully audited access to web applications, SSH, RDP, VNC or Telnet - without an agent.
Team Members (Essentials)
Team Member (Essentials) licenses are necessary for each account user with a unique email address. Each team member should have their own user license. Users can access their Perimeter 81 account on up to 5 devices (desktop, mobile and tablet) at no additional charge. You can have as many team members as you do purchased licenses.Team Members (Premium)
Team Member (Premium) licenses offer all the capabilities of Team Member (Essentials) tier plus the following capabilities: Agentless application Access (up to 20 applications for micro-segmented policy setting), increased Activity audits & reports retention (30 days retention versus 14 days for Essentials), access to shared public gateways (useful for clients traveling abroad that want low latency connections), Single Sign On integrations (integrate with client Identity Provider to provide simpler user authentication), and Always-on VPN (administrators can enforce user endpoints to always keep client connection active).Private Gateways
A private gateway licenses providers a private cloud server dedicated solely to your company. By deploying a private gateway through the management platform your team members can share a single static outgoing IP address only accessible by your organization's authenticated users. Gateways allow for secure and granularly segmented team member access to on-premise network resources, cloud environments, and Zero Trust applications. Each gateway can support normal data traffic for up to 100 concurrent team member users. You may consider adding more gateways to support higher volumes of concurrent users or to add additional geographies where users are located.“Never Trust, Always Verify”
Conventional security models assume everything “on the inside” can be trusted, which is why these legacy technologies are, for the most part, no longer effective.
![]()
Mitigating Too Much Trust
The modern business environment does not guarantee that each endpoint, user and device in the network is secure.
![]()
Overcome Network Challenges
Zero Trust network services and SDP configurations meet network challenges without draining IT resources or budgets.
![]()
Implement User-Centric Security
Network security, policy enforcement and protection are easily implemented for all users, devices, applications and data.
The Simplest, Non-Disruptive Zero Trust Solution
Fully Audited Access
Secure application-level access by fully auditing, recording and monitoring each session. This reduces the attack surface and provides a distributed security solution which operates as a holistic threat protection framework.
Inspect and Log ALL Traffic
Accurately monitor the network by identifying and classifying all traffic, regardless of ports and protocols, encryption or hopping. This eliminates methods that malware may use to hide from detection and provides complete context into applications, associated content and threats.
Least Privilege Access Control
With a least-privileged strategy and strictly enforced access control, organizations can control interactions with resources based on relevant attributes, including application access, user and group identity and the sensitivity of the data being accessed.
Advanced Threat Protection
Comprehensive protection against both known and unknown threats, including threats on mobile devices, is necessary to support a closed-loop, highly integrated defense stature that consistently and cost-effectively enables trust boundaries.
High-Performance Design
Perimeter 81's Zero Trust Application Access minimizes latency and surpasses processing requirements, providing high availability, avoiding loss of service, reducing redundant loads on servers and increasing the uptime of your network.
Comprehensive API Integration
Our comprehensive REST-based API enables quick-and-easy integration with third-party management, automation and orchestration tools, ensuring protection for newly provisioned or relocated virtualized applications.

Zero Trust Application Principles
Perimeter 81’a Zero Trust Application Access protects your network from modern malware, targeted attacks and unauthorised exfiltration of sensitive business data.
With Zero Trust Application Access, organizations can experience several technical and business advantages, including:
![]()
Mitigating Data Loss
Dramatically enhance your security posture and mitigate data loss via visibility, safe enablement of applications and threat prevention.
![]()
Increasing Efficiency
Simplify compliance with highly effective trust boundaries by segmenting sensitive resources into many small perimeters that are secured based on user permissions.
![]()
Enabling Mobility & Virtualization
Increase the ability to accommodate transformative IT initiatives such as cloud computing, infrastructure virtualization, user mobility, social networking and more.
![]()
Reducing TCO
Reduce total cost of ownership (TCO) for IT security by replacing disconnected point products with a single, consolidated security platform.
![]()
Increased Visibility
With audited access to cloud environments, applications and local services, Perimeter 81's Zero Trust Application Access increases security, monitoring and visibility while reducing help-desk support.
![]()
Increased Security
By encrypting all data and filtering unwanted traffic, organizations can prevent sophisticated cyber threats from penetrating perimeter defenses.
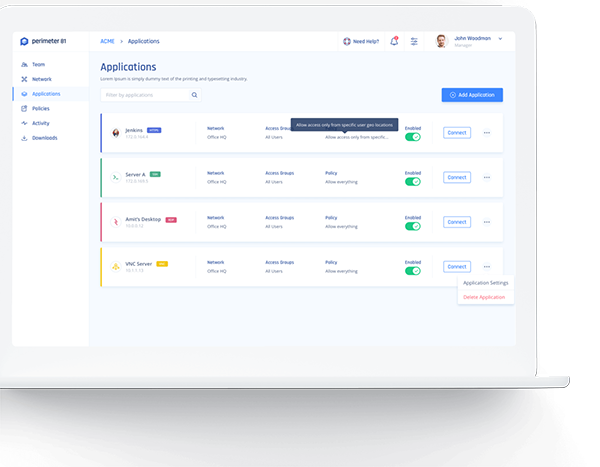
Perimeter 81 - a Must for Zero Trust
Perimeter 81’s Zero Trust Application Access enables access to web applications, SSH, RDP, VNC or Telnet, through resilient IPSec tunnels - without an agent.
With unparalleled visibility, control, and threat protection, our Zero Trust Application Access provides a completely transparent experience for all users without needing to modify existing networks.

